
Jul 17, 2016 Tags: metrocard, programming, reverse-engineering, security Series: decoding-the-metrocard
This post is at least a year old.
Preword: This post has been sitting on my hard drive for over a year. According to the original date on the file I intended to publish it on 6/26/15, or two days after Part 1. I probably shelved it because I didn’t like the format or wasn’t happy with the writing, but I’ve been asked to post it.
This is Part 2 in a series of posts on the MetroCard.
Part 1 provides a brief history of NYC’s Subways and the unique circumstances behind the creation of and the infrastructure behind the MetroCard system, if you’re interested in that.
Beginning on my quest to decode the MetroCard, I came across a fair number of previous attempts with varying degrees of success:

Source: Kyurius via techfreakz
Run by “Kyurius”, this was the first site I came across. Although Kyurius didn’t have any luck actually decoding a MetroCard’s tracks, his site has a few useful points and hypotheses:
Most importantly, Kyurius mentions two other potential sources of information: HOPE (a semiannual hacker conference in NYC), and a 2600 NYC meeting in which MetroCards were discussed. More on those in a bit.
Another site I came across, last updated in 1999 according to its footer, is an information page on the MetroCard written by Daniel Convissor. Most of the information on it is public or common knowledge, but there are a few interesting facts under the ‘How MetroCards Work’ section:
The process by which the card works each time it is used to pay a fare, in approximated order:
- Read expiration date
- If it’s expired, deny access, end transaction
- Read serial number
- Read value of card
- Write new value of card
- Compare this card’s serial number to those on the Negative List
- If it’s on the list, deny access, end transation
- Display value of card on turnstile monitor
- Unlock turnstile
Abbreviated, annotated, and emphasized from the original text.
This was the presentation that Kyurius referenced on their page.
A video from the presentation is still available on YouTube, but finding the actual slides themselves took a fair bit of digging. I eventually found them on a decade-old CCC page (22C3, in particular).
Despite being over a decade old, these slides (and accompanying 2600 articles) still represent the best publicly-available research on the MetroCard format. Joseph Battaglia’s research is meticulous, documenting everything from relevant patents, to the standard hardware used in a MetroCard Vending Machine (MVM), to the field offsets on each magnetic track on the card. He even goes as far as to provide examples of MVM receipts for analysis of serial numbers and location IDs:
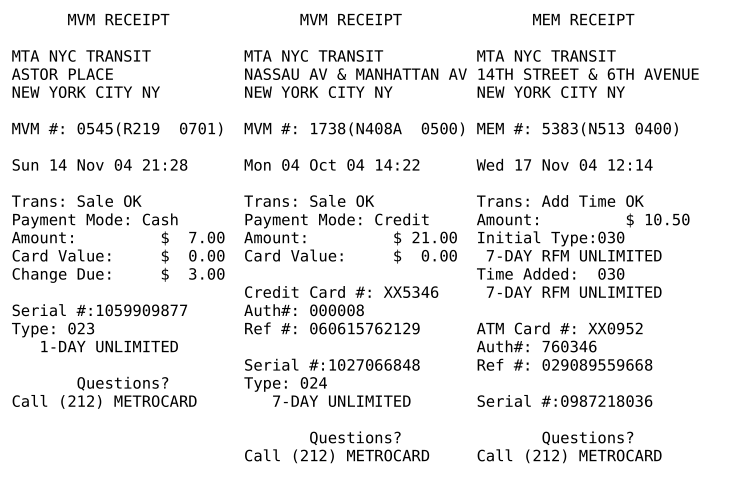
Battaglia also developed some proof-of-concept programs for the customized card reader he built, which can be found in the Spring 2005 issue of 2600 (and online here). There’s simply too much information for me to repeat in this post, so you should really read his articles and slides for the details.
While researching the MetroCard format itself, I came across a few tangentially interesting resources:
Some MTA research (slides) on fare evasion, which has gone down dramatically over the last 25 years (coinciding with the introduction of MetroCards, perhaps not by coincidence). More interestingly, fare evasion via MetroCard spoofing appears to be entirely off the radar - the only evasions mentioned that didn’t involve turnstile/gate hopping were abuses of power (flashing badges) and using turnstile/station keys.
“How To Hack the NYC Subway MetroCard”. This one boils down to an urban myth that I remember hearing (and trying) in elementary and middle school. Essentially, if you bend the track of your metrocard in just the right way, the machine won’t be able to read it and will give you the benefit of the doubt (after a certain number of tries). Although interesting (and possibly even supported by the track layout discovered by Battaglia), it doesn’t really count as a spoof in my book.
Since most of the research referenced above comes from abandoned (or at least unmaintained) pages, I’ve saved it for future reference. You can download an archive here.
This only leaves one final part in the series - my work on decoding the MetroCard. Since it took me a year to publish this part, I’m hesitant to make any promises about when it’ll appear. That being said, I (finally) got my magnetic stripe reader/writer a few months ago and will hopefully be putting it to good use soon.
- William